External threats

Domain registrar

Email, password and phone leaks

Source code, posted on GitHub

Phishing web-sites

Social media

Credentials analysis and generation
Hidden web-pages indexed by search engines


Open ports

Services and applications’ banners

Security controls’ misconfiguration

Access to the restricted data

Public login pages

Default credentials

Vulnerable services
HydrAttack and common security
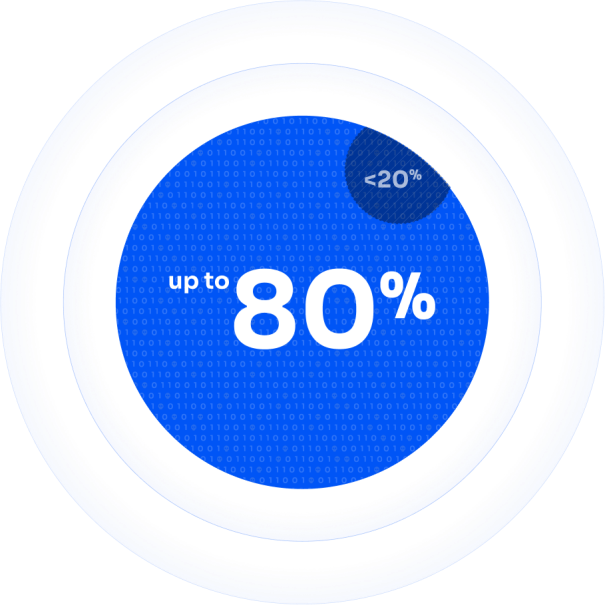
HydrAttack, focused on preventive measures and integrated into traditional approaches, will allow to increase the company’s security protection and maturity level up to 75-80%
Traditional cyber security systems are built around SOC (Security Operational Centre) and Vulnerability Scanners (scanning for outdated services and applications), collectively covering no more than 20% of the attack surface
External attack surface management
HydrAttack works on prevention, identifying risks at early stages, and helps your company prepare and configure its infrastructure for protection against attacks
Providing information about vulnerabilities and misconfigurations allows organizations to take measures to protect themselves and prevent these threats from being realized by attackers. This approach helps to enhance security levels and reduce risks for users and organizations
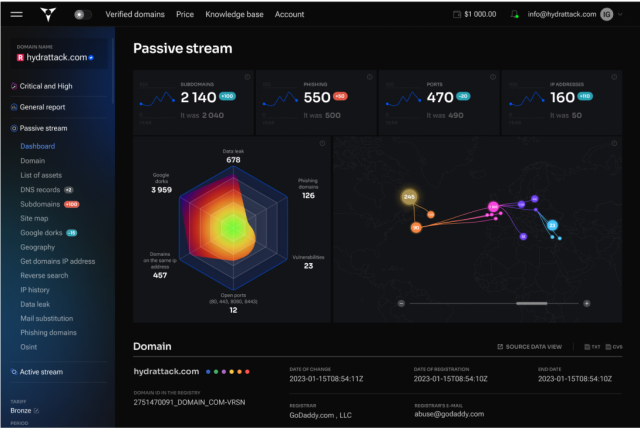
How HydrAttack works
HydrAttack has an unique algorithm that enables rapid and effective detection of external threats. The algorithm consists of more than 30 constantly updated core nodes for information gathering and analysis, which summarize and complement each other
The system is divided into two main streams: passive and active scanning, which detect unmanaged and managed threats, respectively
Process continuity
Threat monitoring and vulnerability scanning are conducted daily, ensuring immediate reaction and, as a result, the security of your system on a continuous basis
If a phishing domain imitating your company was registered yesterday, today you're already aware of it and can implement a set of countermeasures: update anti-phishing rules, conduct awareness training for employees, and initiate an internal investigation regarding this incident
HydrAttack as an ERP system
EASM HydrAttack is made as an ERP system, which allows you not only to generate reports, but also to operate in a full-scale mode
The system allows you to adjust severities and exclude false positives, add or remove assets, determine significance, add comments, and, most importantly, manage tasks – assigning employees to fix issues, setting specific tasks and deadlines, and monitoring execution
Regulatory compliance
HydrAttack ensures the security of your system in accordance with regulatory requirements, international standards, and best global practices
- ISO/IEC 27001:2022 – Information security, cybersecurity and privacy protection — Information security management systems – Requirements
- NIST 800-53 – Security and Privacy Controls for Information Systems and Organizations
- NIST 800-115 - Technical Guide to Information Security Testing and Assessment
- PCI DSS - Payment Card Industry Data Security Standard
- OWASP WSTG - The Web Security Testing Guide of The Open Worldwide Application Security Project
- Center for Internet Security (CIS) Benchmarks - internationally recognized as security standards for defending IT systems and data against cyberattacks
- CVSS - Common Vulnerability Scoring System is used to calculate the Temporal and Environmental scores for an organization's own environment
Cost-Benefit analysis
Using HydrAttack to manage external threats brings significant benefits, especially at scale. Improving the level of security leads to cost reductions and simplified audits, which can significantly overestimate the initial and ongoing costs of implementing and operating systems
- Using HydrAttack allows you to comply with regulatory requirements, which reduces the risk of fines and sanctions
- Using an external solution eliminates the need to purchase and maintain expensive security hardware and software
- Independent assessment from HydrAttack increases customer and partner confidence in your security
- The system helps you to prepare for the audit by providing all the necessary documentation and reports
Our team
- § The Russian Presidential Academy of National Economy and Public Administration, IT Management for Business
- § Military University of the Ministry of Defense, Jurisprudence
- CCISO, EISM, CC, OSCP, Top 10 Global CEH (Master), CNDA, CND
- CVE-2024-24312, CVE-2024-24313, CVE-2024-36821
As an information security expert, my goal is to improve security by identifying vulnerabilities and implementing effective solutions

Over 10 years of experience working in cyber security including
penetration testing of enterprise networks and web application,
establishing information security programs and ensuring the CIA as
well as managing mature information security policies, governance,
awareness, vulnerability and risk assessment and remediation.
As an active member of the Cyber Security community, I have proven
my skills in ethical hacking by identifying and responsibly
disclosing security bugs: remote code execution on Stanford,
HackTheBox, New York University and Martinos Center for Biomedical
Imaging (Massachusetts General Hospital), web admin on Cambridge
and MIT universities; McAfee antivirus bypass.
Knowledge of Bash Scripting, PHP, SQL, Python and C-based program
languages allows me to create my own applications for automation
and optimization company’s security. Close-Circuit Telegram
Vision, Fast Google Dorks Scan, AutoSUID and Domain checker are
some of my applications, which are widely recognized by big
vendors like Splunk, Hakin9 and KitPloit.
Ivan Glinkin
Ideological inspirer and founder of HydrAttack- § Krasnodar Higher Military School, Comprehensive Information Objects Protection
- § Military Academy of Communications, Networks Communication and Switching Systems
- ISO 27001 Lead Auditor, ISO 27001 Internal Audit, GOST 57580 Auditor, CEH
Managing mature information security policies, awareness, vulnerability and risk assessment, and their subsequent remediation is the main focus of my work

Over 10 years of experience in cybersecurity, including
penetration testing of corporate networks and web applications,
developing information security programs, and ensuring the data
confidentiality, integrity, and availability.
Managing mature information security policies, awareness,
vulnerability and risk assessment, and their subsequent
remediation is the main focus of my work
As an expert in information security, my goal is to enhance the
security level of business processes through effective information
security risk assessment, vulnerability identification, and the
implementation of effective solutions.
I am an active and regular speaker at international events,
including CODE IB and SB PITER, speaking on topics of information
security and OSINT (open source intelligence).
Vladimir Makarov
Cyber security expert- § Bauman Moscow State Technical University, Informatics and Control Systems, Counteraction to Technical Reconnaissance
- § Military Academy of Communications, Networks Communication and Switching Systems
Team coordination, cyber strategy development, and testing of corporate networks and web applications to ensure data confidentiality and integrity

An expert in information security with extensive experience of
more than 15 years, I focused on infrastructure penetration
testing and possessing numerous certifications that confirm my
knowledge and skills in this area. My career includes work in
various organizations where I was involved in information
protection and vulnerability management. Currently, I am the head
of department responsible for handling cyber security
vulnerabilities and incidents, coordinating a team of penetration
testers, developing security strategies, and participating in key
projects.
My skills cover a wide range of technologies, including tools and
software solutions in the area of data protection and monitoring.
My work involves penetration testing of corporate networks and web
applications, developing information security programs, and
ensuring the confidentiality, integrity, and availability of data.
I apply my abilities in the search and analysis of information,
including through open sources (OSINT), for the effective conduct
of investigations and the provision of information security.
Dmitry Kalinin
Cyber security expert- § Bachelor of Science in Networking and Security, Arab Open University (AOU), Lebanon
- CRTO, GMOB, OSWE, OSCP, Offshore, ICSI
As a cybersecurity expert, my mission is to safeguard systems by uncovering vulnerabilities and deploying robust security measures

Louay is a Cyber Security Expert with over 5 years of experience,
proficient in various aspects of cybersecurity, including
vulnerability assessment and penetration testing for network,
infrastructure, web, and mobile applications. He excels in red
teaming, source code review, threat hunting, social engineering,
and configuration review.
Louay has conducted comprehensive cybersecurity assessments,
including application security, industrial control systems,
physical security, vulnerability management, and network security
architecture reviews. He has executed social engineering and
awareness campaigns across multiple financial and public sectors
in the region.
His work includes configuration reviews for network devices,
operating systems, and databases, as well as performing numerous
penetration tests targeting various levels, using advanced
techniques. Louay has delivered multiple security presentations at
events such as LEAP and various internal sessions.
Louay Farchoukh
Cyber security expert- § Moscow State Aviation Institute, Design Engineer
- § Academy of Management of the Ministry of Internal Affairs of Russia, Management
Over 20 years of experience working in internal affairs, including participation in official trips and international conferences

A security expert with extensive experience in investigation
activities and information analysis.
Over 20 years of experience working in internal affairs, including
participation in official trips and international conferences. I
hold a first-class specialist qualification and have been awarded
for outstanding achievements.
Skills in collecting, analyzing, and processing information using
various software tools. Key expertise in investigation work and
ensuring security in the financial sector.
Currently, I head the comprehensive information aggregator
DataMe.online for the automatic search, collection, analysis, and
summarization of information.




