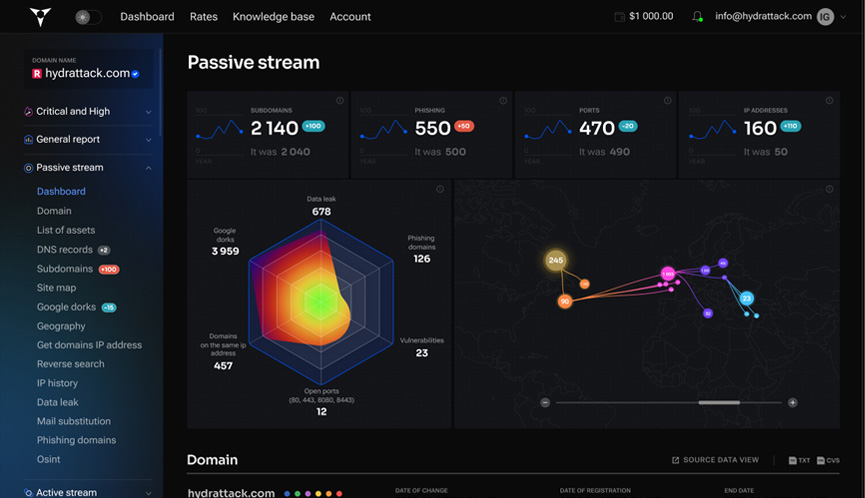
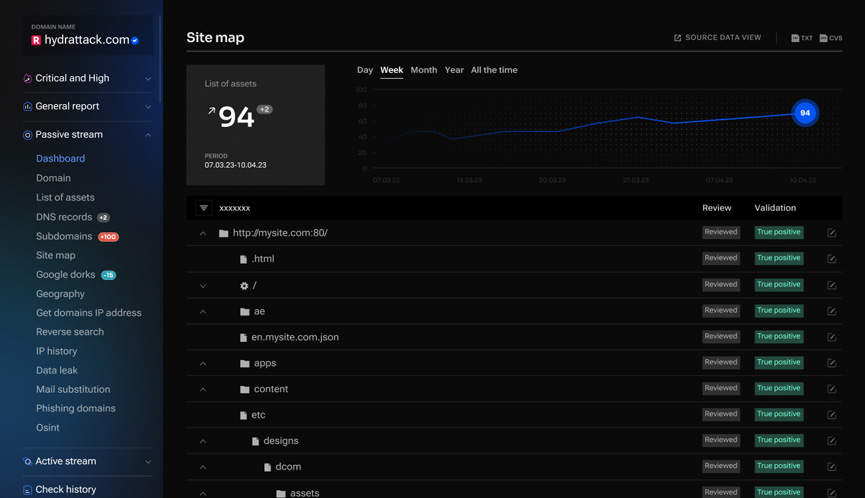
Data leak
Phishing
domains
domains
Vulnerabilities
Open ports
(80, 443, 8080, 8443)
(80, 443, 8080, 8443)
Domains
on the same ip
address
on the same ip
address
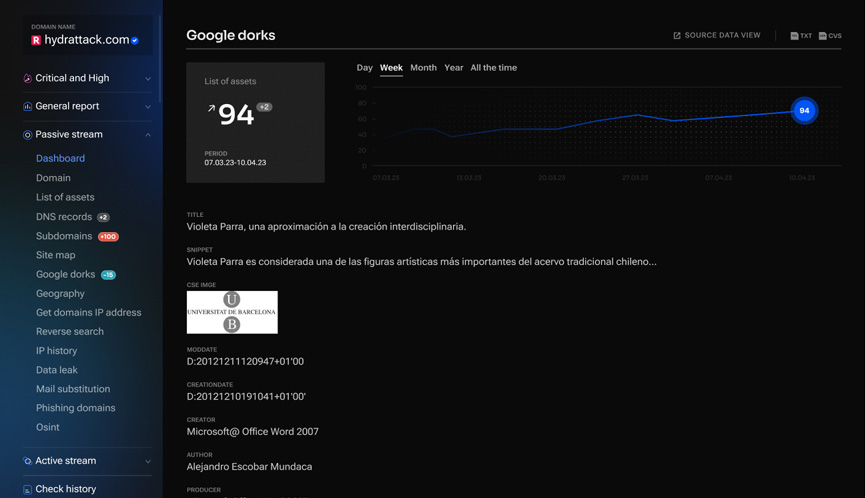
Google
dorks
dorks
External attack
surface management system
318
web applications scanned
292939
threats found
An innovative risk management platform designed to help identify and mitigate web application risks in completely new ways
Platform features
- Review
- Graph analysis
- Attribution
- Data leaks
- Sitemap
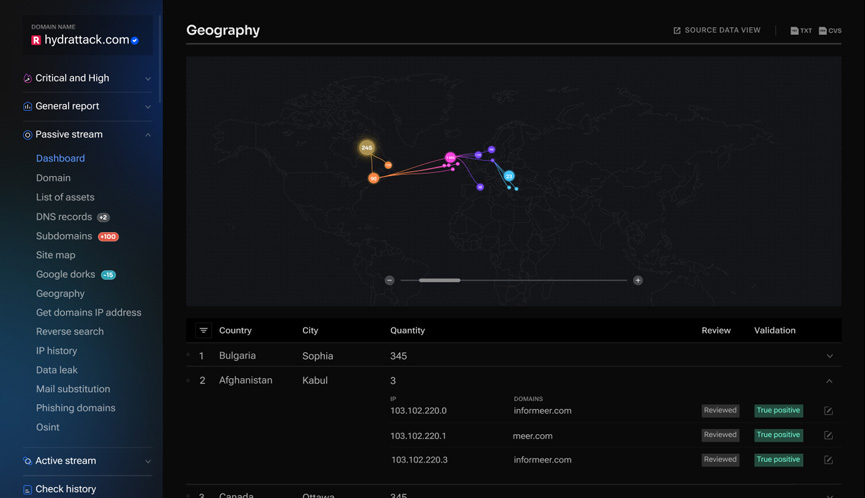
- Geografy
To ensure your organization's infrastructure doesn't become the first line of defense against attackers, proactively prevent information security threats.
We will help you to reduce your risks
8 out of 10 companies has high severity threads as a result of the first scan
Check the quality of the result in our social networks, there you will find more results
About platform
Domain
Passive stream
Active stream
Analytics
CMS + report
HydrAttack is a new external attack surface management system. The idea of EASM is not new in the market, so it will be quite difficult to gain market share. Instead of copying other solutions, we collected them all and added new uniq features other did not.
HydrAttack is divided into 2 main streams that are not implemented by competitors: passive and active workflows. Thus, our system will find unmanaging and managing flaws of your company by indirectly and directly interacting with your domain.